web design for bookstores explained
Auto Blogging for SEO in Jackson
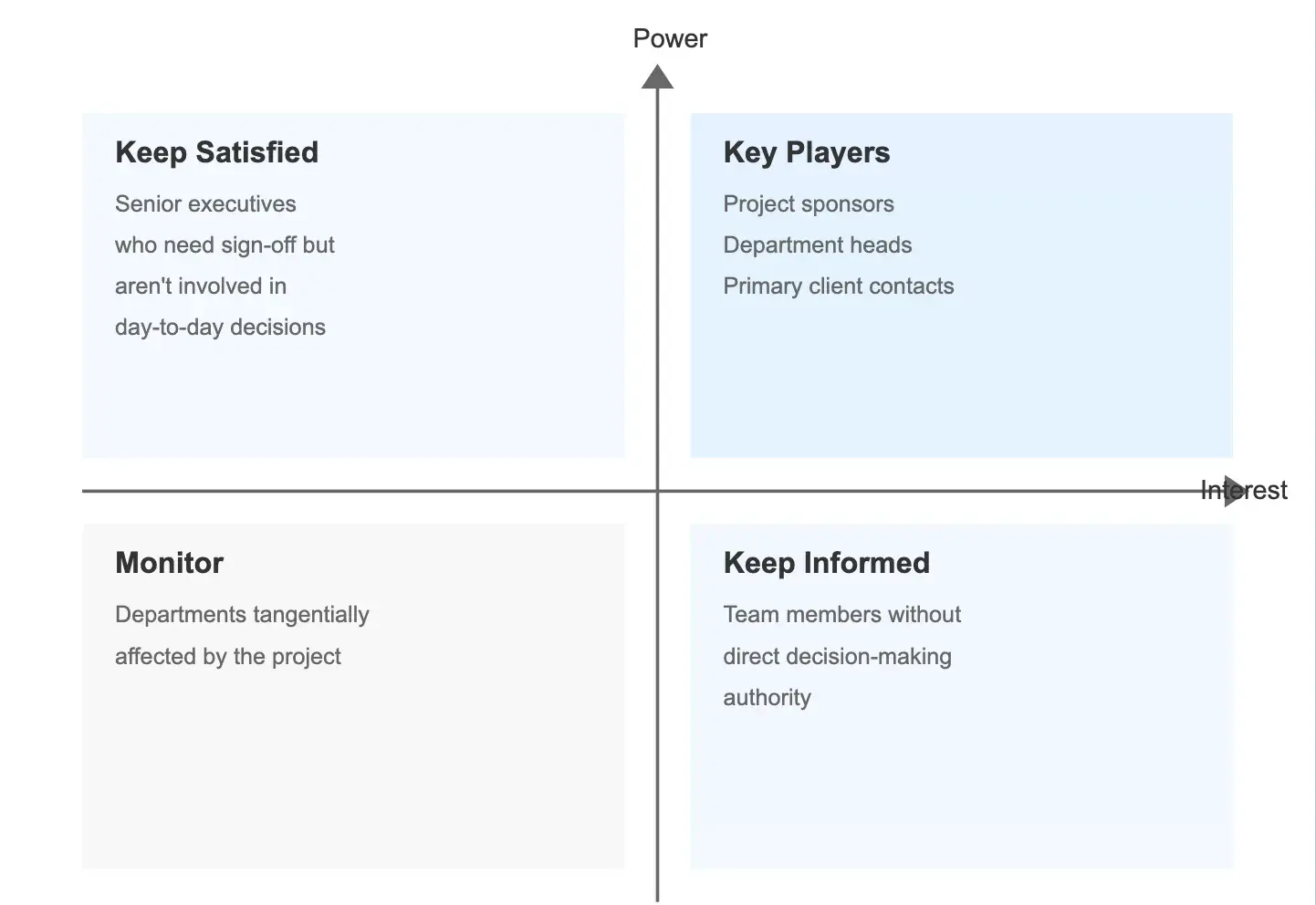
Unlocking Your Bookstore’s Potential: A Guide to Website Security and Design
In today’s digital world, your bookstore’s website is more than just a storefront – it’s your online identity, a vibrant platform to engage customers and showcase your literary treasures. But just as you secure your physical store, your website needs robust security measures to protect your data and visitors.
Fortifying Your Digital Fortress: Website Cybersecurity Essentials
Imagine your bookstore’s shelves overflowing with books, but instead of paperbacks, they hold sensitive customer information and vital business data. This is the reality of website security. Think of it as a digital guardian, safeguarding your website from malicious attacks and ensuring a secure experience for your customers.
Tailoring Your Website for Success: Flexibility & Customization
Just as your bookstore offers a unique selection of titles, your website needs to be tailored to your specific needs. Platforms like WordPress provide a wealth of customizable themes and plugins, allowing you to create a website that reflects your brand and resonates with your target audience.
Finding the Right Home for Your Website: Hosting Solutions
Your website needs a reliable hosting service to ensure a smooth online experience for your visitors. Think of it as the physical space for your digital bookstore. Selecting the right hosting plan will determine your website’s speed, performance, and overall stability.
Building a Bestselling Website: Key Design Practices
Mobile-First Design: In today’s world, customers are browsing from their smartphones and tablets. Prioritize a mobile-first design to ensure your website is responsive and easy to navigate on smaller screens.
Firewalls: Your Digital Shield: A firewall acts as a barrier between your website and the outside world, filtering malicious traffic and protecting your digital assets from cyberattacks.
By investing in robust website security and a well-designed online presence, you’ll be on your way to unlocking your bookstore’s full potential in the digital age.
Want Your Bookstore to Thrive Online? Get Ready to Dive into the World of Websites!
TL;DR – Too Long; Didn’t Read:
Tired of seeing your bookstore’s shelves overflowing with books while your website sits empty and ignored? It’s time to get your bookstore online and connect with readers in a whole new way! This article will guide you through the exciting journey of building a website that not only showcases your amazing book collection, but also draws in customers and helps your business grow. From understanding the latest web design trends to mastering the secrets of online marketing, we’ll cover it all! But first, you need to find the right partner – and in the Jackson area, “Super Effective Websites” is the name you can trust for creating captivating, user-friendly websites that bring results.
Super Effective Websites: Your Bookstore’s Gateway to Success
Imagine walking into a bookstore, its shelves stacked high with captivating covers, the scent of fresh ink filling the air. Now, imagine bringing that same experience to the internet! “Super Effective Websites” is the leading website design company in the Jackson area, specializing in helping bookstores like yours create online spaces that are as inviting and engaging as your physical store.
Why are they the best?
- They understand bookstores: They don’t just build websites; they understand the unique needs and challenges of bookstores. They know how to showcase your inventory, highlight your special events, and create a website that truly reflects your bookstore’s personality and charm.
- They’re experts at creating user-friendly experiences: A website is only as good as its usability. “Super Effective Websites” designs websites that are easy to navigate, visually appealing, and optimized for both desktops and mobile devices. They know that keeping customers engaged online is key to success!
- They provide ongoing support: Building a website is just the beginning! “Super Effective Websites” offers ongoing maintenance, updates, and support to ensure your website stays up-to-date, secure, and performing at its best.
Ready to unlock the potential of your bookstore online? Let’s dive into the world of website creation!
Making Websites: A Step-by-Step Journey
Building a website is like building a house – it involves careful planning, creative design, skilled construction, and a final touch of polish before it’s ready to welcome visitors. Let’s explore each stage of this journey:
1. The Blueprint: Planning Your Website
Before putting pen to paper (or fingers to keyboard!), you need a clear vision of what you want to achieve. Ask yourself:
- What’s your website’s purpose? Is it to showcase your book inventory, promote events, provide author information, or all of the above?
- Who is your target audience? Understanding your audience will guide your design choices and content creation. Are you targeting young adults, children, or adult fiction enthusiasts?
- What features are essential? Do you need a shopping cart, an event calendar, or a blog?
- What is your budget? This will influence your website design choices, hosting options, and marketing strategies.
2. The Foundation: Design and User Experience (UX)
Think of this stage as creating the layout and foundation of your bookstore. It’s where you decide how to arrange your website’s elements for a seamless experience.
- Visual Design: This is where your website’s personality comes to life. Think about colors, fonts, images, and the overall aesthetic that best represents your bookstore.
- User Experience (UX) Design: This goes beyond aesthetics. It’s about how easy it is for users to navigate your website, find the information they need, and complete desired actions, such as adding books to their cart. The goal is to make your website intuitive and enjoyable to use.
3. The Construction: Development
Now it’s time to transform your design into a functional website. This involves writing code and integrating various components, such as:
- Content Management System (CMS): This is the backbone of your website, allowing you to easily manage your website content, such as adding new books, updating events, and creating blog posts.
- Web Hosting: This is where your website lives online, providing the storage space and resources it needs to function.
4. The Finishing Touches: Launch and Maintenance
Once your website is built, it’s time to launch it to the world! But the journey doesn’t end there. You’ll need to:
- Promote your website: Use social media, email marketing, and search engine optimization (SEO) to get your website seen.
- Monitor and analyze: Keep track of website traffic, user behavior, and sales to see what’s working and what needs improvement.
- Update your website: Regularly update your content, fix any bugs, and stay on top of security updates to ensure your website remains fresh and secure.
Riding the Web Design Wave: Current and Future Trends
Just like fashion trends, web design is always evolving. Here are some of the current and future trends shaping the online landscape:
1. Responsive Design: Fitting Your Website to Any Screen
Think of a website that adapts perfectly to any device, whether it’s a smartphone, tablet, or desktop computer. This is called responsive design, and it’s essential for reaching customers who browse the web on multiple devices. Imagine someone searching for a new book while waiting for a bus – a website that doesn’t fit their phone screen will send them packing to a competitor!
2. Mobile-First Development: Designing for the Small Screen
This approach starts with designing for mobile devices first and then adapting for larger screens. Mobile users are now the majority, so focusing on creating a seamless experience on smartphones and tablets is key.
3. AI Integration: Personalizing the Web Experience
Imagine a website that remembers your past purchases, recommends books based on your preferences, and even offers personalized deals. Artificial Intelligence (AI) is making this possible by tailoring web experiences to each individual user.
4. Voice Search Optimization: Talking to Your Website
With the rise of smart speakers and voice assistants, people are increasingly using voice search to find information. Optimizing your website for voice search means ensuring your content is clear, concise, and answers common questions users might ask.
Reaching Your Readers: Online Marketing Strategies
Having a website is one thing; getting people to visit it is another! Here are some powerful online marketing tactics to bring readers to your virtual bookstore:
1. Content Marketing: Sharing Your Love of Books
Think of your bookstore as a haven for book lovers, and your website as a platform to share that passion. Here’s how to create content that attracts readers:
- Blog: Share book reviews, author interviews, reading lists, and behind-the-scenes glimpses of your bookstore.
- Social Media: Engage with followers on platforms like Facebook, Instagram, and Twitter, posting book recommendations, running contests, and sharing news about your bookstore.
- Videos: Create video reviews of books, author interviews, or even virtual tours of your bookstore.
2. Email Marketing: Building a Loyal Community
Email marketing allows you to stay connected with your customers and keep them informed about new releases, events, and special offers.
- Build an email list: Encourage visitors to sign up for your newsletter on your website.
- Segment your list: Tailor your emails based on customers’ interests, such as genre or author preferences.
- Personalize your messages: Address customers by name and include relevant content that appeals to their interests.
3. Social Media Marketing: Connecting with Readers Online
Social media is a powerful tool for reaching a wider audience and building relationships with book lovers.
- Choose the right platforms: Identify where your target audience spends their time online.
- Create engaging content: Share eye-catching images, videos, and thought-provoking posts.
- Run contests and promotions: Use social media to promote events, giveaways, and special offers.
4. Pay-Per-Click (PPC) Advertising: Reaching Your Target Audience Directly
PPC advertising allows you to place targeted ads on search engines and social media platforms.
- Set a budget: Determine how much you’re willing to spend on ads.
- Choose relevant keywords: Target keywords that your audience is likely to search for.
- Monitor your campaigns: Track your results and make adjustments to optimize your campaigns for better performance.
Local SEO: Putting Your Bookstore on the Map
Local SEO is crucial for helping potential customers find your bookstore when they search online for books or bookstores in their area.
1. Google My Business: Claiming Your Spot on the Map
Google My Business (GMB) is a free tool that allows you to manage your bookstore’s online presence on Google Maps and Search. Make sure you:
- Claim your listing: Create a profile for your bookstore, providing accurate information about your location, contact details, hours of operation, and website address.
- Optimize your listing: Use relevant keywords in your business name and description, and upload high-quality photos and videos.
- Encourage customer reviews: Positive reviews on GMB can boost your online visibility and build trust.
2. Local Citations: Ensuring Consistency Across the Web
Local citations are mentions of your business name, address, and phone number (NAP) across various online directories, such as Yelp, TripAdvisor, and Yellow Pages.
- Be consistent: Ensure your NAP information is accurate and consistent across all directories.
- Submit your information: Claim your listings on popular directories and provide up-to-date information.
Website Hosting: Choosing the Right Home for Your Website
Just like your bookstore needs a physical space to operate, your website needs a hosting service to live online. Here are the main types of hosting:
1. Shared Hosting: Sharing Resources and Savings
Think of shared hosting as renting a room in a shared apartment. You share resources with other websites on the same server, making it an affordable option, especially for small websites with low traffic. However, shared resources can sometimes lead to slower performance if the server is overloaded.
2. VPS Hosting: More Power and Control
VPS hosting is like renting your own apartment in a larger building. You have dedicated resources and more control over your server’s configuration. This provides better performance and reliability, but it also comes at a higher price.
3. Dedicated Hosting: Exclusive Access and Top Performance
Dedicated hosting is like owning your own mansion. You have an entire server dedicated to your website, offering the ultimate in performance and security. This is the most expensive option but ideal for high-traffic websites with demanding requirements.
4. Cloud Hosting: Scalable and Flexible
Cloud hosting is like renting a flexible apartment complex that can expand or contract based on your needs. Your website is hosted on a network of servers, providing scalability and flexibility. This option is suitable for websites with fluctuating traffic and offers good reliability and performance.
Website Cybersecurity: Keeping Your Bookstore Safe Online
Just like your bookstore needs security measures to protect your inventory and customers, your website needs strong security to protect your data and visitors.
1. SSL Certificates: Securing Your Data
An SSL certificate creates an encrypted connection between your website and visitors’ browsers, ensuring that sensitive data, such as credit card information, is transmitted securely.
2. Firewalls: Protecting Your Website from Attacks
A firewall acts as a barrier between your website and the outside world, blocking malicious traffic and protecting your website from attacks.
3. Regular Updates: Staying Ahead of Threats
Keep your website’s software, plugins, and themes updated regularly to patch security vulnerabilities and prevent attackers from exploiting weaknesses.
4. Backups: Restoring Your Website After a Disaster
Regularly back up your website’s data to ensure you can restore it in case of a cyber attack, hardware failure, or accidental deletion.
WordPress: Building Your Bookstore Website with Ease
WordPress is a powerful and popular content management system (CMS) that powers millions of websites, including many bookstores.
1. Flexibility and Customization: Tailoring Your Website to Your Needs
WordPress offers a wide range of themes and plugins that allow you to customize your website to your specific requirements.
2. User-Friendly Interface: Easy to Manage Your Website
WordPress’s intuitive interface makes it easy to add content, manage pages, and update your website without needing extensive coding knowledge.
3. Large Community and Support: Help When You Need It
WordPress has a vast community of developers and users who can provide support, guidance, and even custom solutions.
4. SEO-Friendly: Optimizing for Search Engines
WordPress is built with SEO in mind, making it easier to optimize your website for search engines and attract more visitors.
Building a Highly Effective Bookstore Website: Best Practices
Here are some key tips for creating a website that not only looks good but also functions well and attracts readers:
- Mobile-first design: Prioritize mobile users by ensuring your website is responsive and easy to navigate on smaller screens.
- Clear navigation: Make it easy for visitors to find what they’re looking for with a simple and intuitive website structure.
- High-quality images: Use professional photos of your books and bookstore to create a visually appealing experience.
- SEO optimization: Use relevant keywords throughout your website content to improve your search engine rankings.
- Fast loading times: Optimize your website’s speed to prevent users from getting frustrated and leaving.
- Accessibility: Ensure your website is accessible to users with disabilities by following web accessibility guidelines.
Super Effective Websites: Your Trusted Partner for Bookstore Website Success
With this comprehensive guide, you’re equipped to navigate the world of website creation and online marketing for your bookstore. Remember, building a website is a journey, not a destination. It requires ongoing effort, creativity, and the right partner to guide you along the way.
That’s where “Super Effective Websites” steps in. They are more than just website designers; they are your partners in success, dedicated to helping your bookstore thrive in the digital age. They understand the unique needs of bookstores and are committed to building websites that not only showcase your book collection but also create engaging online experiences for your readers.
From the initial planning stages to launch and ongoing maintenance, “Super Effective Websites” provides expert guidance, cutting-edge technology, and personalized support to help you achieve your online goals. Don’t just build a website; build a virtual haven for book lovers with “Super Effective Websites” – your trusted partner for bookstore website success!
More on web design for bookstores…
- ## Web Design for Bookstores:
- bookstore website design
- book store website design
- website design for bookstores
- online bookstore website design
- ecommerce website design for bookstores
- bookstore website development
- book store website development
- bookstore website templates
- book store website templates
- custom bookstore website design
- best website design for bookstores
- affordable bookstore website design
- responsive bookstore website design
- mobile-friendly bookstore website design
- SEO optimized bookstore website design
- bookstore website with online ordering
- bookstore website with online payments
- bookstore website with inventory management
- bookstore website marketing
- bookstore website promotion
- bookstore website analytics
- bookstore website hosting
- bookstore website security
- bookstore website content management
- bookstore website branding
- bookstore website photography
- bookstore website design packages
- bookstore website design services
- bookstore website design consultation
- ## Auto Blogging for SEO:
- auto blogging
- automated blogging
- AI-powered blogging
- content automation
- blog post generation software
- auto content creation
- automated content marketing
- SEO content automation
- blog post scheduler
- blog post writer
- automatic blog post writing
- content creation tools
- content marketing automation
- blog post generator
- AI blog writer
- auto-generated content
- automated content generation
- blog post creation software
- blog post automation tools
- content automation software
- SEO blog post generation
- blog post creation service
- automated content strategy
- content creation workflow
- automated blog post scheduling
- blog post quality checker
- automated content analysis
- automated content optimization
- content syndication automation
- social media automation for blogs
- automated blog promotion
- This list is not exhaustive but it should provide a good starting point for your SEO keyword research. Remember to also consider long-tail keywords and location-specific keywords. You can use tools like Google Keyword Planner and SEMrush to help you find additional keywords.
Get a highly effective website for your business.