
- Shop
- (Untitled)
- Smart Shopper
- Deals
- Gift Ideas
- Lifestyle
- New Discoveries
-
Featured
-
Featured
- Recent
-
Select Page
Are you able to protect your digital world from emerging online dangers? With Cyber threats are becoming increasingly subtle Every day, protecting your data has never been more important.
In this article we will find out how Prison IPan OSINT search engine, allows you to stay one step ahead of cybercriminals. We will provide an explanation of what Prison IP is, how it works, and why using open source intelligence (OSINT) is a game changer in detecting and combating threats.
Whether or not you are an expert in cybersecurity or simply want to ensure that your online presence is secure, learning how to use tools like Jail IP could make all the difference.
Index material topic material
Prison IP is an OSINT search engine designed for cybersecurity tasks, much like assessing attack surfaces and understanding potential threats.

It constantly collects and updates data in real time, using AI technology to detect dangerous IP addresses and domains. The risk is then assessed on a 5-level scale. The information is organized with filters and tags to make it easier to verify. Additionally, it can be integrated with other devices and methods (e.g. Cisco, AWS Marketplace, wordpress, Zabbix) using an API for seamless integration.
To really understand what Prison IP To do this, you first need to know what an OSINT search engine is.
OSINT stands for Open Provide Intelligencewhich involves the accumulation and analysis of data from public goods such as the Internet, social media and public information.
An OSINT search engine is a tool specifically designed to help like-minded buyers find and analyze information that is available to the public all through various online goods.
Search engines like Google and Yahoo are used relentlessly by cybersecurity professionals, investigators, journalists, and researchers to find the most important information, identify potential threats, or disclose hidden details.
They often offer sophisticated options that allow buyers to search multiple platforms at once, apply specific filters, and even track ongoing movements.
The importance of Open Intelligence Information (OSINT) In the field of cybersecurity, it cannot be overstated, as it plays a crucial role in helping organizations and professionals identify and organize threats, increase situational awareness, and make informed decisions.
That’s why it’s so important…
Through the use of monitoring publicly available data—much like social media, forums, and websites—cybersecurity teams can spot first signs of potential attacksvery similar to discussions about vulnerabilities or planned actions. This allows them to take proactive defensive measures.
Tools that analyze open source information are essential discover weaknesses in an organization’s digital infrastructure. This includes looking for exposed servers, unprotected databases, and misconfigured ways that attackers can exploit them. Address problems promptly can prevent violations.
During a cybersecurity incident, the accumulation of information from publicly available assets helps understand the attacker’s methods, apparatus and motivationsThis information is the most important for assess the scope of the attackunderstand compromised methods and develop an effective response methodology.
Throughout the penetration testing reconnaissance segment, accumulating open source data some purposes help simulate real-world attacks. This allows penetration testers to identify potential weaknesses in defenses and recommend improvements.
Monitoring public mentions of a brand, products or employees can alert organizations to potential threats such as phishing websites, fake social media profiles or leaked data. This early warning helps provide protection and organize the reputation of the crowd.
Open Source Intelligence It is also valuable to ensure Regulatory compliance. Monitoring for information leaks, unauthorized disclosures, or any public information that might indicate non-compliance is essential. It is similarly useful in due diligence mergers, acquisitions or partnerships anywhere, providing confidence in the cybersecurity of potential partners.
Through the use of data collection and analysis from various assets, organizations gain a broader view of the cybersecurity landscapeThis complicated situational awareness helps them stay one step ahead. emerging threatsindustry provisions and cybercrime movements.
Since the information comes from public goods, it is often further convenient compared to other intelligence methods. Organizations can gather valuable information without having to expensive goods or gain access to confidential data.
Public domain information It is widely used by regulatory control companies for collect evidence and track criminal movementsIn cybersecurity, it helps trace the origins of attacks, identify perpetrators, and drive legal action against cybercriminals.
Monitoring your supply chain for vulnerabilities or threats is a critical tool. Understanding the risks associated with third-party suppliers or partners helps protect the crowd from potential attacks.
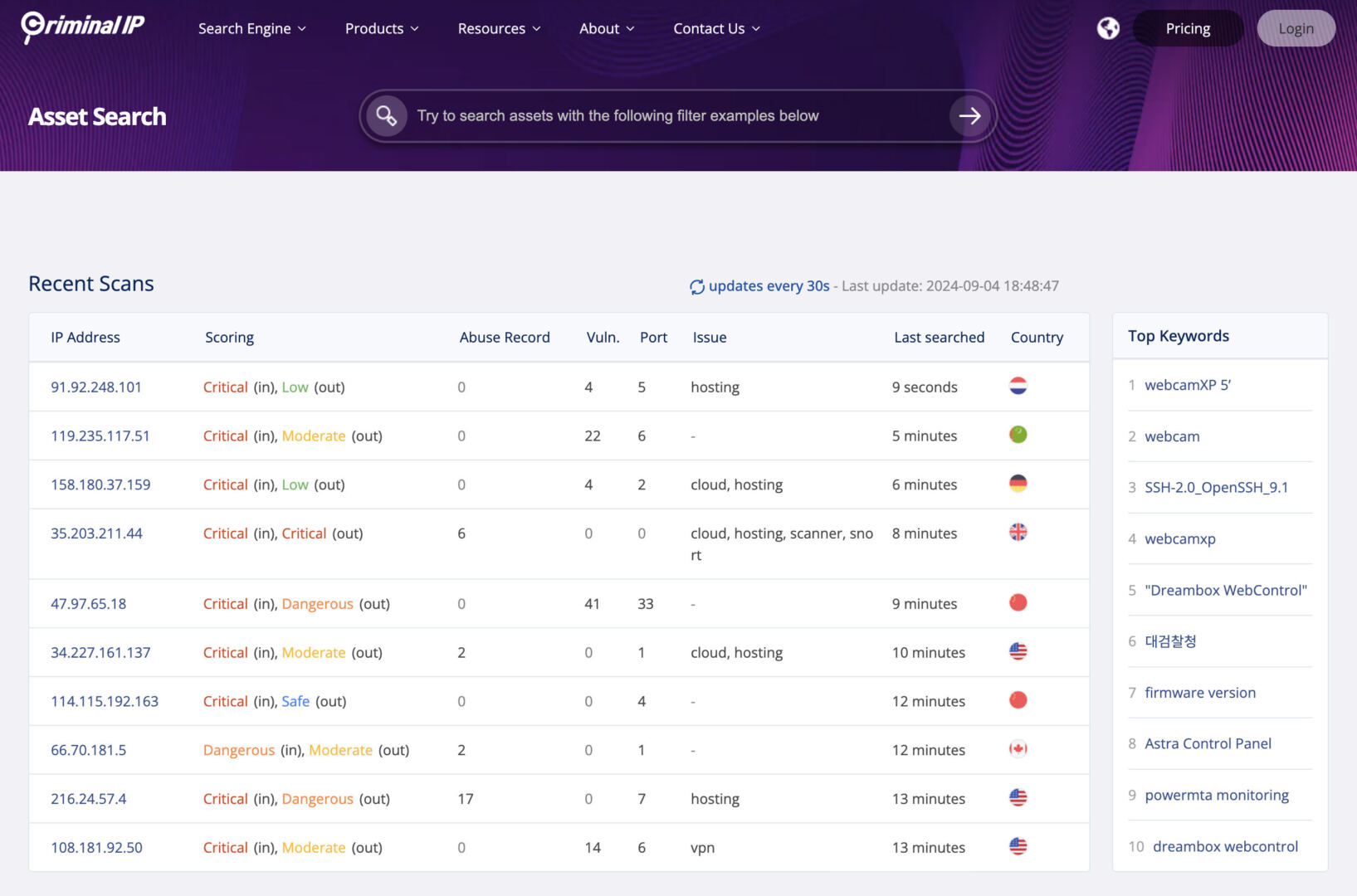
Now, once again to Prison IPOSINT search engine. IP Jail provides a difficult apparatus to explore vulnerabilities and track all types of internet-connected gadgets, along with IP addresses, domains, IoT gadgets and commerce control modes (ICS).
Here’s a quick info, a general look at what everyone does:
| Search for resources | It provides probability score, comparable asset information, abuse history, and comparable vulnerability information to reveal the threat of a searched IP. However, you will immediately search for vendor identification with a keyword or search for CVE amount to search for comparable IP. |
| Space Research | It scans your home information in real time to provide information including whether or not it is a phishing link, a malicious link, and the validity of the certificate, along with a probability score. |
| Image Search | It provides information about images of assets at risk of cyber threats when searched under different conditions very similar to RDP, phishing, webcam, VNC and RTSP. |
| Search for exploits | It no longer scans for Special Vulnerabilities and Exposures (CVE) and provides detailed information, along with the actual hijacking codes, on a vendor-by-vendor basis. |
| Banner Explorer | It provides information on tagged threats related to products and services very similar to cryptocurrencies, databases, and IoT gadgets. |
| Vulnerability Intelligence | Provides details on exposed vulnerabilities, labeled by CVE ID and product identification, contributing to proactive monitoring and surveillance. |
| Statistics | It provides statistical graphs of VPN, proxy, Tor, scanner and malicious IPs for the last 7 days, displaying the status of suspicious anonymous IPs and offering development data. |
| Section Analysis | When searching by keyword, you can also filter by country, supplier, ASN, product identifier, port number, and favicon hash, allowing you to view statistics for each elegance. |
| Maps | View data geographically, showing the location of IPs, domains or assets, helping to assess the scope of potential attacks. |
Jail IP is a tool that you will have access to via its API to collect threat intelligence on any software, server, or home connected to the Internet. It is useful in various areas of cybersecurity, much like attack surface management, penetration testing, vulnerability and malware analysis, along with investigations and research.
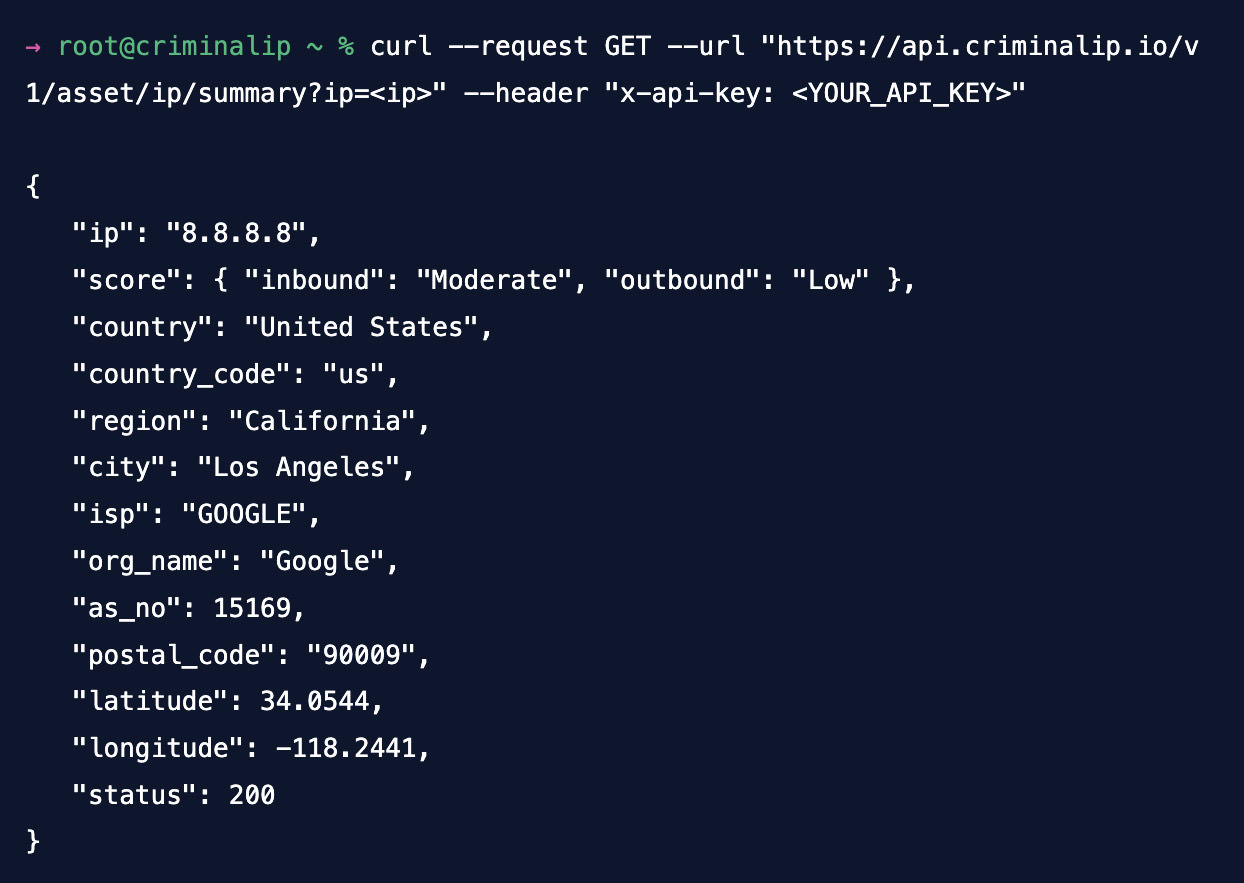
For example, when a new vulnerability or ransomware is discovered, Jail IP helps you find out which PCs or servers are at risk or are already infectedYou will also be able to check if any IP addresses or domains you may be using are vulnerable.
Additionally, prison IP scanning for Malicious and phishing URLs generated by hackers in real time, allowing you to investigate threats without having to take immediate action.
The Jail IP API makes it easy to combine these options in your own ways. Using an API key for authentication, you will have access to multiple endpoints to scan IP addresses, domains, and URLs for potential threats. The endpoints provide key information such as likelihood ratings, geolocation, and a history of malicious activity, all returned in JSON format for empty integration.
The API leverages simple HTTP requests and allows you to automate threat detection, helping you stay on top of cybersecurity risks.
To learn more about Jail IP API integration, see the GitHub Reference web page or the Best Observe web page.
But that’s not all: let’s take a look at the plans offered by Jail IP and their pricing:
For further details, please see the pricing webpage.
The post Using Prison IP to Search for Cyber Risks appeared first on Hongkiat.
Source: https://www.hongkiat.com/blog/criminal-ip-osint-cybersecurity-threat-detection/
[ continue ]
wordpress Maintenance Plans | wordpress hosting
Learn more